Don't be the next cyber victim! Secure your business and its future.
What is good practice today does not represent good practice tomorrow
As COVID-19 becomes endemic, cyber threats have also become pervasive and sophisticated. SMEs that can detect breaches quickly, respond decisively and have a cybersecurity culture among employees, have the best chances of recovering quickly and surviving.
What is a CISO?
As your business goes digital, it is vital to have someone looking out for security and privacy to ensure business resilience. The Chief Information Security Officer (CISO) is that someone who is responsible for security operations, securing the business, its technology, and its initiatives, and leading the business’s information security strategy. An effective CISO needs to have both a strong business acumen and technical background. He/she also needs to be a good listener and communicator. In the world of information security, there is a growing need for people who know how to communicate, empathise, and talk the language of their non-security colleagues.
|
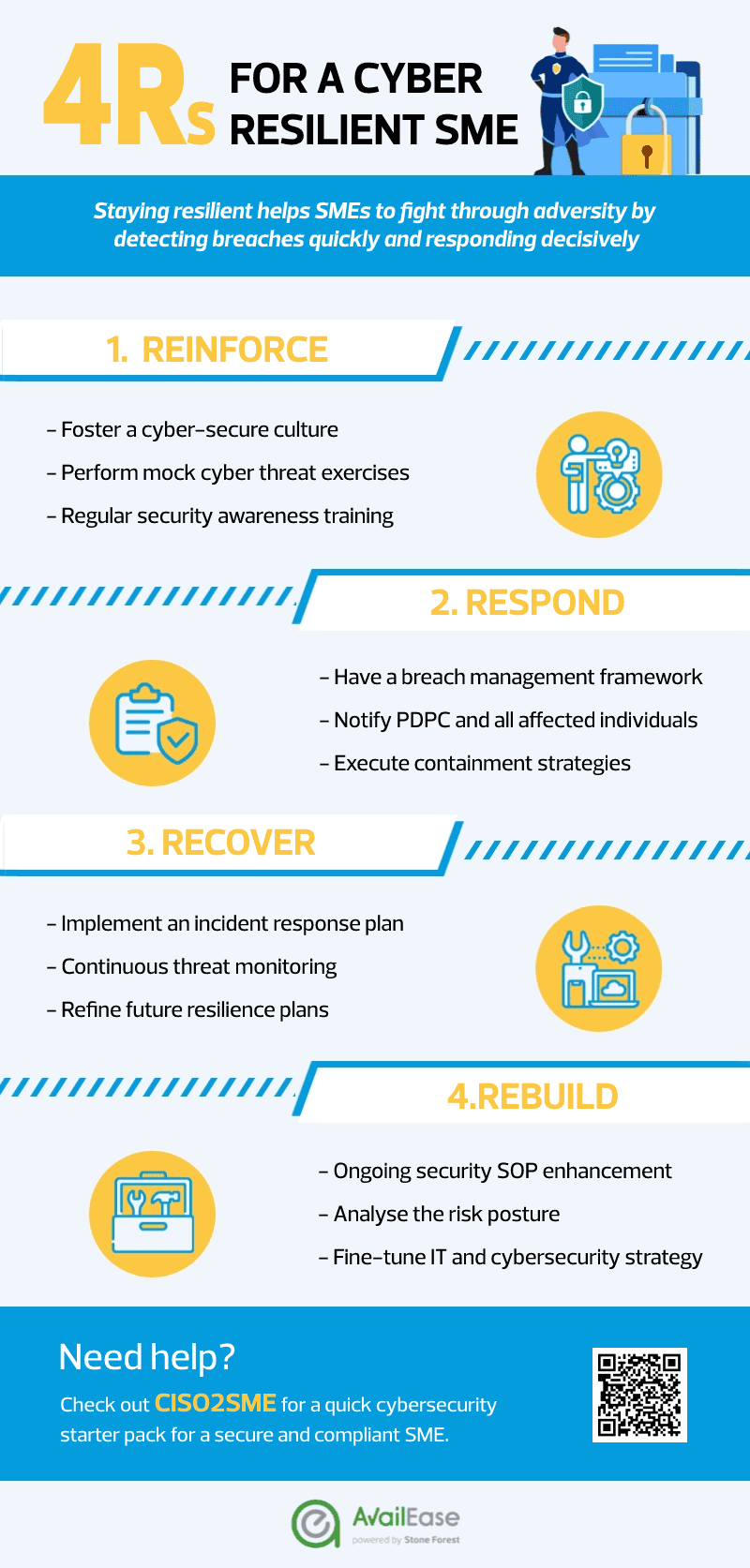 CISO2SME - 4R's Approach CISO2SME - 4R's Approach
(Click to view) |
Developing a Cyber Resilience Plan - The 4R's Cybersecurity Approach
1 | REINFORCE
Firewalls and security policies are only effective if employee vigilance is present. You can reinforce the most vulnerable link in your organisation's cybersecurity defences by fostering a cyber-secure culture among employees. While making improvements to your existing security infrastructure, you should also perform mock cyber threat exercises to assess the risk level among employees. Once you have that baseline, you can then effectively address the awareness gap and keep everyone up-to-date with the latest regulatory requirements, by educating employees with regular security awareness training with PDPA updates.
2 | RESPOND
A well-documented data breach management framework is key to ensure that everyone does not panic and knows the appropriate procedures to follow in the event of a breach. To minimise costly and negative consequences, your framework should cover processes that facilitate the quick identification and assessment of the breach. It is also mandatory under the PDPA to notify PDPC and all affected individuals of the severity and impact of the breach. Be quick to execute containment strategies to prevent further damage and data breach.
3 | RECOVER
In addition to safeguards, businesses should implement an incident response plan. The objective here is to minimise business disruptions by promptly restoring and managing impacted systems to full functionality. The incident response team will need to decide when is it best for operations to be restored, test and verify that infected systems are fully restored, continue to monitor for malicious activity, and validate the recovery. It is important refine future resilience plans based on lessons learned to avoid another similar incident in the future.
4 | REBUILD
Cyber resilience necessitates ongoing monitoring and development, in addition to strategy, training, and safeguards. Analyse the risk posture and fine-tune IT and cybersecurity strategy to better protect the company from future threats by closing any cybersecurity gaps. Not one plan is 100% attack proof so the ability to return to normal operations quickly can assist an organisation in bearing the brunt of the damage.
Need help? Check out IMDA's Cyber Essentials Initiative
Protect your operations and customers against common cyber-attacks by ensuring the presence of good cyber hygiene practices. Up to 70% co-funding support available.
Begin by assessing your cyber health and improve your cyber resilience with Cyber Essentials. We'll help develop a Cybersecurity Health Plan tailored for your needs. Contact us to find out more!